Oracle released the scheduled critical security updates for its Java SE Runtime Environment software and, once again, released two versions.
The updates contain (thirteen) 13 new security fixes for Oracle Java SE of which (nine) 9 of these vulnerabilities may be remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password.
Unwanted "Extras"
Although most people do not need Java on their computer, there are some programs and games that require Java. In the event you need to continue using Java, How-to Geek discovered a little-known and unpublicized option in the Java Control Panel to suppress the offers for the pre-checked unwanted extras that Oracle has long included with the updates. Although the Ask Toolbar has been removed, tha does not preclude the pre-checked option for some other unnecessary add-on.Do the following to suppress the sponsor offers:
- Launch the Windows Start menu
- Click on Programs
- Find the Java program listing
- Click Configure Java to launch the Java Control Panel
- Click the Advanced tab and go to the "Miscellaneous" section at the bottom.
- Check the box by the “Suppress sponsor offers when installing or updating Java” option and click OK.
Windows XP
For information on Java support for Windows XP, organizations and individuals who must continue using Windows XP and have Java installed are referred to the Oracle blog post, The future of Java on Windows XP (Henrik on Java).Update
If Java is still installed on your computer, it is recommended that this update be applied as soon as possible due to the threat posed by a successful attack.Download Information
Download link: Java SE 8u101Java SE 8u102 can be found here. Select the appropriate version for your operating system.
Verify your version: http://www.java.com/en/download/testjava.jsp
Notes:
- UNcheck any pre-checked toolbar and/or software options presented with the update. They are not part of the software update and are completely optional.
- Starting with Java SE 7 Update 21 in April 2013, all Java Applets and Web Start Applications should be signed with a trusted certificate. It is not recommended to run untrusted/unsigned Certificates. See How to protect your computer against dangerous Java Applets
Critical Patch Updates
For Oracle Java SE Critical Patch Updates, the next scheduled dates are as follows:- 18 October 2016
- 17 January 2017
- 18 April 2017
- 18 July 2017
Java Security Recommendations
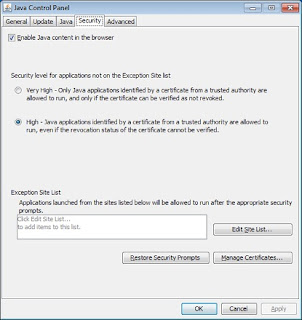
For those people who have desktop applications that require Java and cannot uninstall it, Java can now be disabled in Internet Explorer. See Microsoft Fix it to Disable Java in Internet Explorer.1) In the Java Control Panel, at minimum, set the security to high.
2) Keep Java disabled until needed. Uncheck the box "Enable Java content in the browser" in the Java Control Panel.
Instructions on removing older (and less secure) versions of Java can be found at http://java.com/en/download/faq/remove_olderversions.xml
References
- Java SE 8u101 Update Release Notes
- Java SE 8u102 Update Release Notes
- Java, The Never-Ending Saga
- Oracle Critical Patch Update Advisory
- Oracle Quality Assurance Blog
- Critical Patch Updates and Security Alerts

Remember - "A day without laughter is a day wasted."
May the wind sing to you and the sun rise in your heart...