The MSRC Blog reported that Microsoft conducting investigations into how this vector may affect Microsoft products. In addition, Microsoft released KB Article 2264107, which includes a new CWDIllegalInDllSearch registry entry to control the DLL search path algorithm:
"The update allows the administrator to define the following on a system-wide or a per-application basis:That may be fine for IT Professionals, but what about home computer users? If, like me, you use WinPatrol PLUS, you have at your fingertips a simple method of adding protection from the DLL (CWDIllegalInDllSearch) vulnerability. Bill Pytlovany added the entries to include in WinPatrol Registry Monitoring Scripts . With this simple entry, WinPatrol will notify you if anyone tries to create and change this value from a non-zero value.
- Remove the current working directory from the library search path.
- Prevent an application from loading a library from a WebDAV location.
- Prevent an application from loading a library from both a WebDAV, as well as a remote UNC location."
Edit Note: The instructions have been updated to change the following question by ky331 and response by Bill Pytlovany after his discussions with some folks at Microsoft. (See the Comments below.)
The steps are simple. Start by launching WinPatrol, select the "Registry Monitoring" tab and click Add:

As illustrated in the simple steps below, a new window will open to add the item to be monitored.
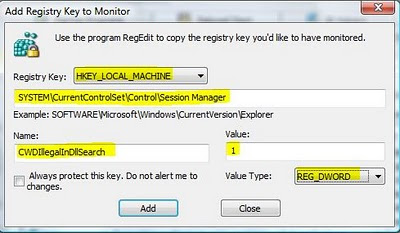
SYSTEM\CurrentControlSet\Control\Session Manager
The results:

It is that simple with WinPatrol PLUS! Unemployed and unable to afford a license? Be sure to check out WinPatrol Supports Unemployed Job Seekers.
References:
- BillP Studios: WinPatrol Registry Monitoring Scripts
- DLL Hijacking (KB 2269637) – the unofficial list (Peter Van Eeckhoutte)
- KB 2264107: A new CWDIllegalInDllSearch registry entry is available to control the DLL search path algorithm
- ISC SANS: DLL hijacking vulnerabilities
- Firefox, uTorrent, and PowerPoint hit by Windows DLL bug
- Knowledge Base article 2264107
- MSRC Blog: Microsoft Security Advisory 2269637 Released
- SR&D Blog: More information about the DLL Preloading remote attack vector
- TechNet: Security Advisory 2269637
Clubhouse Tags: Clubhouse, Microsoft, Windows, Security, WinPatrol, Information, Advisory, Vulnerabilities, How-to, WinPatrol,





4 comments:
I'm not sure that I'm following the WinPatrol "protection"...
As I read it, Scotty will sound an alert any time the CWDIllegalInDllSearch registry item is not set to 0 (here, 0=follow the default .dll path).
However, the Microsoft Advisory indicates that the non-default value(s) of 1 (or 2)
"Blocks a DLL Load from the current working directory if the current working directory is set to a WebDAV folder" (or remote folder, respectively).
So it seems to me that these non-default values offer more protection/blocking.
Thank you for your comment. After discussions with some folks at Microsoft they feel setting the value to 1 or 2 would best protect users who wanted to use WinPatrol to let them know of any change.
Ultimately however they recommend scrolling down the article http://support.microsoft.com/kb/2264107 and having folks download the appropriate fix that Microsoft has made available.
When I ran the fix on my system, it actually changed the value to 1.
Thanks again for your comment.
Bill
DLL hijacking vulnerability, which was released last week, results in some programs no longer working properly.So you should use application protection for this.
Post a Comment